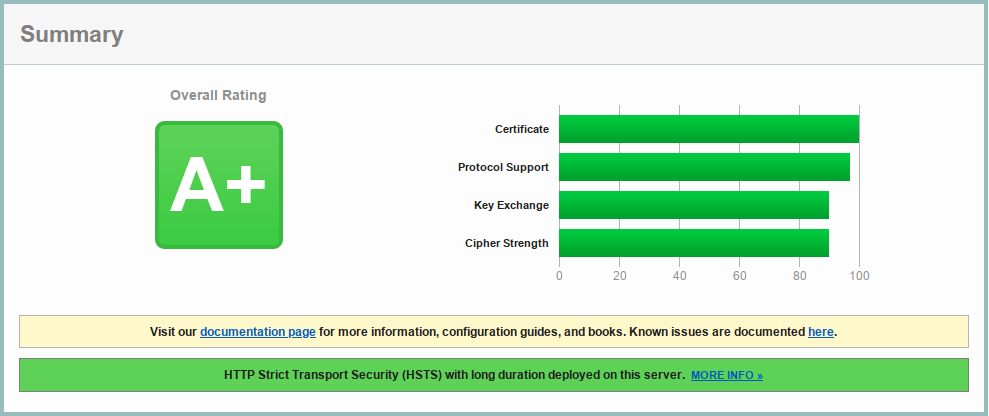
Just a reminder for myself which cipher suites to use to be compliant with PCI DSS, NIST, and HIPAA guidelines. The configuration below also excludes weak cipher suites.
ssl_protocols TLSv1.1 TLSv1.2; ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:!DSS'; ssl_session_cache shared:SSL:10m; ssl_session_timeout 1d; ssl_prefer_server_ciphers on; ssl_session_tickets off; ssl_dhparam /etc/nginx/dhparams.pem; ssl_stapling on; ssl_stapling_verify on; ssl_certificate_key /etc/letsencrypt/live/domain.com/privkey.pem; ssl_certificate /etc/letsencrypt/live/domain.com/fullchain.pem; ssl_trusted_certificate /etc/letsencrypt/live/domain.com/chain.pem;
/etc/nginx/dhparams.pem is the pre-defined DH group ffdhe2048 (see RFC 7919 and Mozilla Wiki).
This configuration differs from Mozilla SSL Configuration Generator’s Intermediate Profile in the following:
- TLS 1.0 is disabled (PCI compliance).
- TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ECDHE-RSA-CHACHA20-POLY1305) is disabled to comply with HIPAA and NIST guidelines.
- TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA (ECDHE-RSA-DES-CBC3-SHA), TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA (EDH-RSA-DES-CBC3-SHA), TLS_RSA_WITH_3DES_EDE_CBC_SHA (DES-CBC3-SHA) are disabled to comply with PCI DSS, HIPAA, and NIST guidelines.
- TLS_RSA_WITH_AES_128_GCM_SHA256 (AES128-GCM-SHA256), TLS_RSA_WITH_AES_256_GCM_SHA384 (AES256-GCM-SHA384), TLS_RSA_WITH_AES_128_CBC_SHA256 (AES128-SHA256), TLS_RSA_WITH_AES_256_CBC_SHA256 (AES256-SHA256), TLS_RSA_WITH_AES_128_CBC_SHA (AES128-SHA), and TLS_RSA_WITH_AES_256_CBC_SHA (AES256-SHA) are disabled, because those cipher suites are weak according to SSL Labs.
Note: when using certbot, for the certificate to include ‘OCSP Must Staple’ flag, --must-staple command line option should be used.
TLS Configuration for nginx to Get A+ in HTBridge and SSL Labs Tests