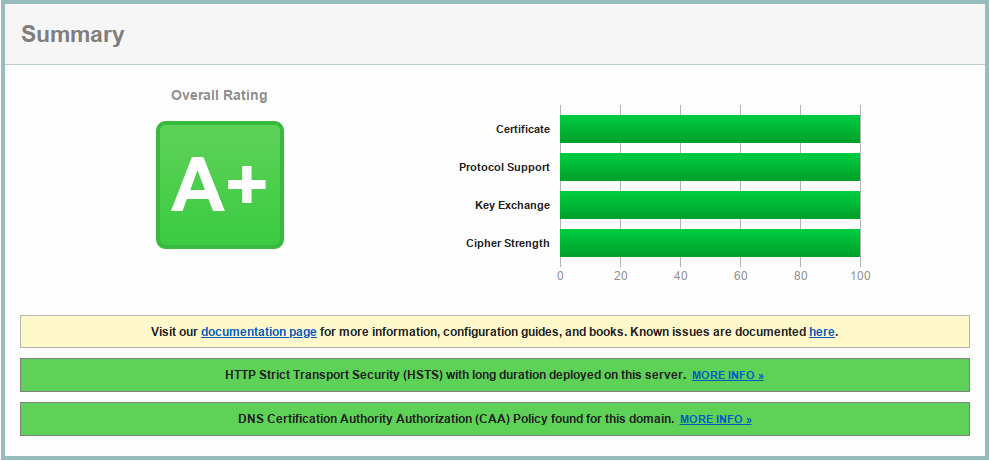
This article provides a configuration for nginx that successfully passes SSL Labs tests with A or A+ mark (see below), and 100% score for all metrics (certificate, protocol support, key exchange, cipher strength).
Notes:
- Key size must be at least 4096 bytes (for certbot, use
certbot certonly --rsa-key-size 4096). - To get A+, HSTS must be enabled (
add_header Strict-Transport-Security "max-age=63072000;" always;); to include the domain into the HSTS preload list, please see the submission requirements. - Contrary to what some other people say, OCSP stapling is not required to get all 100. If you need OCSP stapling, the correct configuration is
ssl_trusted_certificate /etc/letsencrypt/domain/live/chain.pem; ssl_stapling on; ssl_stapling_verify on;, and it is desirable to invokecertbotwith--must-staplecommand line option. X-Frame-Options: DENYandX-Content-Type-Options: nosniffheader are not required to get all 100.
Using Only Elliptic Curve Ephemeral Diffie-Hellman Key Exchange
No need to set up Diffe-Hellman parameters (dhparams.pem).
ssl_protocols TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers 'ECDHE:!AES128:!CAMELLIA128'; ssl_ecdh_curve secp384r1;
Notes:
- For my system,
ECDHE:!AES128:!CAMELLIA128expands toECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-CCM8:ECDHE-ECDSA-AES256-CCM:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-CAMELLIA256-SHA384:ECDHE-RSA-CAMELLIA256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA. ECDHE-RSA-AES256-SHA(andECDHE-ECDSA-AES256-SHA) is actually a TLSv1 cipher; however, if it is disabled, Android 5.0.0, Android 6.0, Firefox 31.3.0 ESR / Win 7, and IE 11 / Win Phone 8.1 will fail to connect (Server sent fatal alert: handshake_failure).
Using More Cipher Suites
ssl_protocols TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers 'ECDHE:DHE:!AES128:!CAMELLIA128:!SEED'; ssl_ecdh_curve secp384r1; ssl_dhparam /etc/nginx/dhparams.pem;
Notes:
- For my system,
ECDHE:DHE:!AES128:!CAMELLIA128:!SEEDexpands toECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-CCM8:ECDHE-ECDSA-AES256-CCM:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-CAMELLIA256-SHA384:ECDHE-RSA-CAMELLIA256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-DSS-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES256-CCM8:DHE-RSA-AES256-CCM:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA256:DHE-RSA-CAMELLIA256-SHA256:DHE-DSS-CAMELLIA256-SHA256:DHE-RSA-AES256-SHA:DHE-DSS-AES256-SHA:DHE-RSA-CAMELLIA256-SHA:DHE-DSS-CAMELLIA256-SHA. - See note about
ECDHE-RSA-AES256-SHA(andECDHE-ECDSA-AES256-SHA) above. DHE-RSA-AES256-SHA,DHE-DSS-AES256-SHA,DHE-RSA-CAMELLIA256-SHA, andDHE-DSS-CAMELLIA256-SHAare SSLv3 ciphers; they can be safely disabled (i.e.,ECDHE:DHE:!AES128:!CAMELLIA128:!SEED:!SSLv3).- Diffie-Hellman group size should be at least 4096 bits (
dhparams.pemcan be taken from here).
See also: SSL Labs SSL Server Rating Guide
Final notes:
- Although both configurations are strong and secure, they are quite restricted: not all clients (for example, Android 4.x, IE 8-10 on Win 7, Java 7, Safari 6.0.4 on OS X 10.8.4) will be able to connect.
- According to HTBridge, both configurations are PCI DSS compliant.
- According to HTBridge, neither configuration follows HIPAA or NIST guidelines (both require TLSv1.1, and both object to
ECDHE-RSA-CHACHA20-POLY1305,DHE-RSA-CHACHA20-POLY1305,DHE-RSA-AES256-CCM8,DHE-RSA-AES256-CCM, andDHE-RSA-CAMELLIA256-SHAcipher suites; also, both HIPAA and NIST guidelines require OCSP stapling).
How to Get Maximum Score in SSL Labs Test (nginx)